Creating a Honeytoken User in Office 365¶
🕵🏻♀ v️🕵🏻♂¶
As part of my current project to harden Office 365, I have proposed to my partner in “Don’t Do” Crimes that we should conduct some phishing and other fun little war games to work out how we can implement some more proactive security controls Spy vs. Spy style.

So as part of my pre-emptive strike I decided to implement a honey token user in Office 365 - which he doesn’t know about… yet, but I mean in a 3 user directory so most changes are easy to spot 👀 when you’re looking.
For anyone unfamiliar with Office 365’s honey tokens it is a part of Microsoft Defender for Identity (formerly Azure Advanced Threat Protection) which requires Enterprise Mobility + Security E5/A5, Microsoft 365 E5/A5, Microsoft 365 E5/A5 Security, and Microsoft Defender for Identity for Users.
I’m not going to get to into the pre-requisites because that alone is a blog post and a half, but you can find out more about Microsoft Defender for Identity pre-requisites from Microsoft!
But before I get to into the detail:
🍯 What is a honey token?¶
Honey tokens also referred to as canary tokens (because they are like a canary in a coal mine… but work in the reverse) can bea piece of information that allows a blue team to implant a trap in the system. This could be a file, an image bug, a fake system (like a honey pot) or a fake user, or service account.
It’s important to note though that for honey tokens to be useful to you they should be enticing to an attacker - you want them to find them and trigger them, tokens should also be detectable, if their usage goes unnoticed because of a lack of logging and monitoring they lose all value. Finally, honey tokens should have no value other than detecting their use - if there is any meaningful value to the token if an attacker gets hold of one it potentially spells game over.
In 2018 I did a couple of talks and a blog post going into a bit more detail about the Thinkst Canary Tokens and how they can be leveraged in various systems - you can check that out here. But there are other systems that exist that do the same thing.
🪛 Setting up the Honey Token¶
The first step was creating a Group Managed Service account on the domain controller so I could connect Microsoft Defender for Identity to the on-prem AD.
This was probably the hardest part of the whole configuration because I was trying to decide if a standalone Managed Service account would be better but knowing we plan to add another DC in the next 6 months it made more sense to use the gMSA.
Important
You will need to reboot your DC after installing .NET 4.7.
Next I had to install the sensor of the AD, this was also straight-forward - transfer the binary over to the DC and double click to install…

Warning
There is a known issue if you are running a virtual DC (Domain Controller) on ESXi. If you’re planning on deploying Microsoft Defender for Identity in an Enterprise/Business environment I’d also recommend checking out this list of known issues Troubleshooting Microsoft Defender for Identity Known Issues.
Once the agent is installed you’ll need to create some local users that will be assigned as “honey token” accounts in our instance we started with a domain admin account and a service account for backups that is also Kerberoastable.
I set these accounts up like we would any other user/service account in the domain. This was especially important because it’s a small DC so any major deviations may standout as obvious bait. In addition to ensure we align to the three principals of a good honey token, the passwords are strong because we need to have some assurance that accounts that look like domain administrators cannot have their passwords cracked. The good thing is that as far as documentation goes, Microsoft Defender for Identity will detect and alert on any authentication attempt associated with these accounts irrespective of their success.
Finally, once your accounts are created you can register them in the Azure Advanced Threat Protection Portal > Configuration > Entity tags panel, by searching the user, clicking the plus and hitting save at the bottom of the page.
🚨 Sounding the Alarm¶
Once configured I tried running runas /netonly /user:domain.localrebecca-da and runas /user:domain.localrebecca-da neither of which created an alert.
However, when I tried to connect to our Domain Controller via RDP that sent alarm bells flying in both Microsoft Defender for Identity and Cloud App Security which is good because getting back to the Microsoft Defender for Identity portal was a PITA here are some of the examples:
🔎 Microsoft Defender for Identity Portal¶
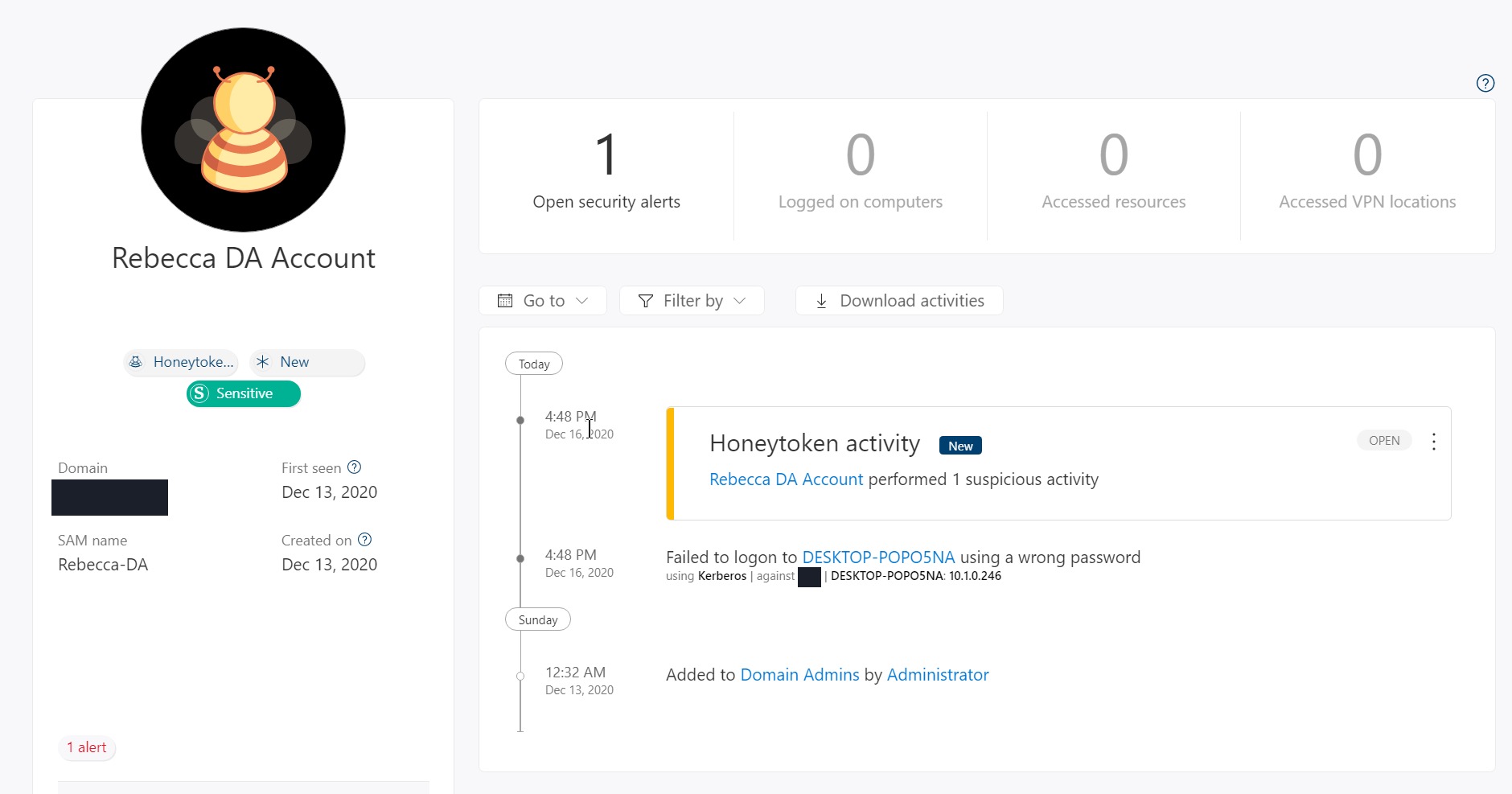
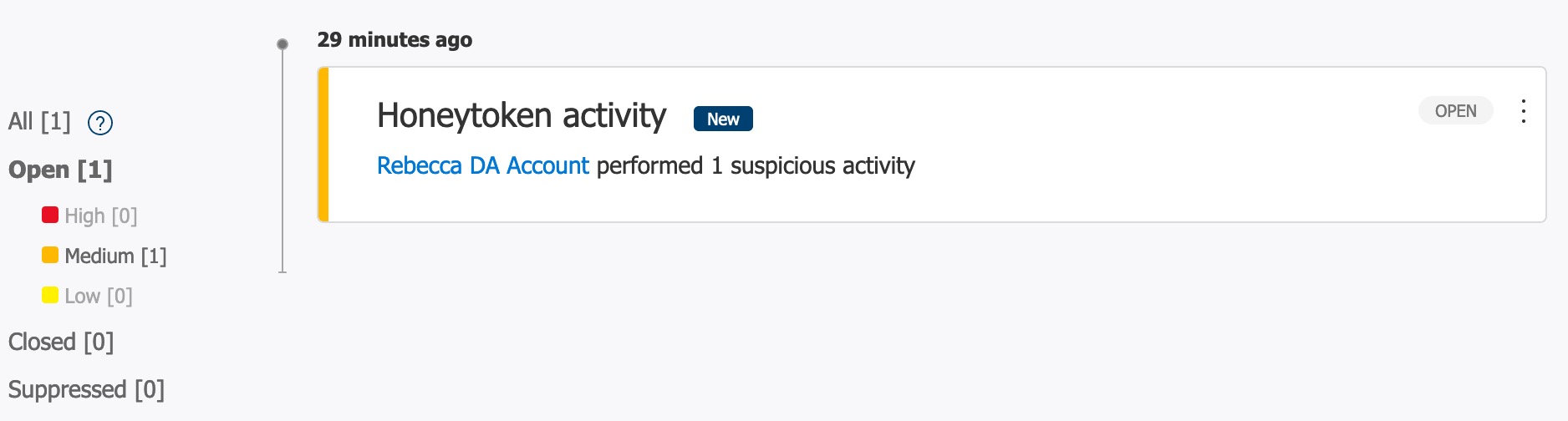
When you first navigate back to the Microsoft Defender for Identity Portal you will be shown a timeline of events that are rated:
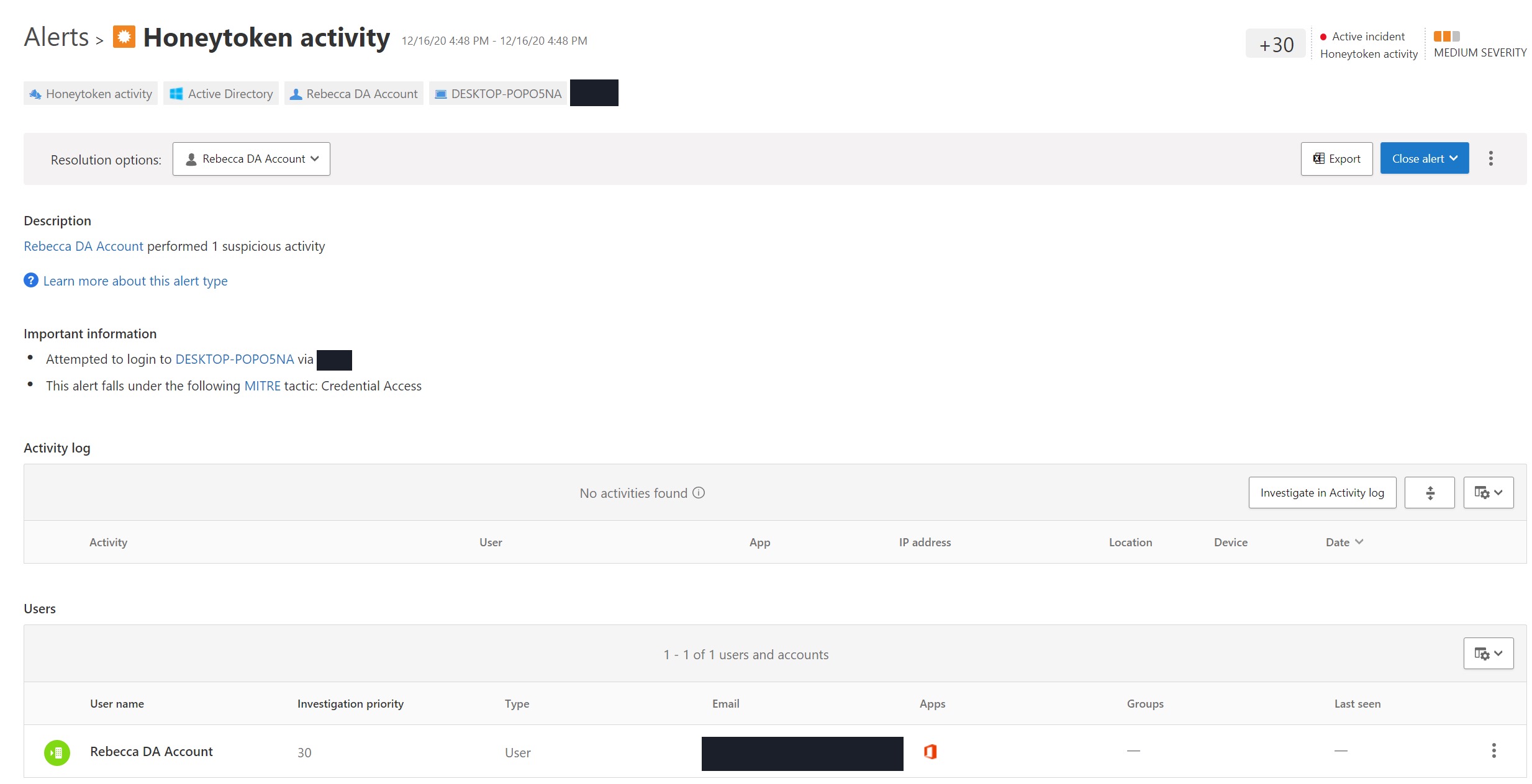
From here you can click into the activity and see more detail about which user was performing what activity, the result (success or failure) and what they were trying to access:
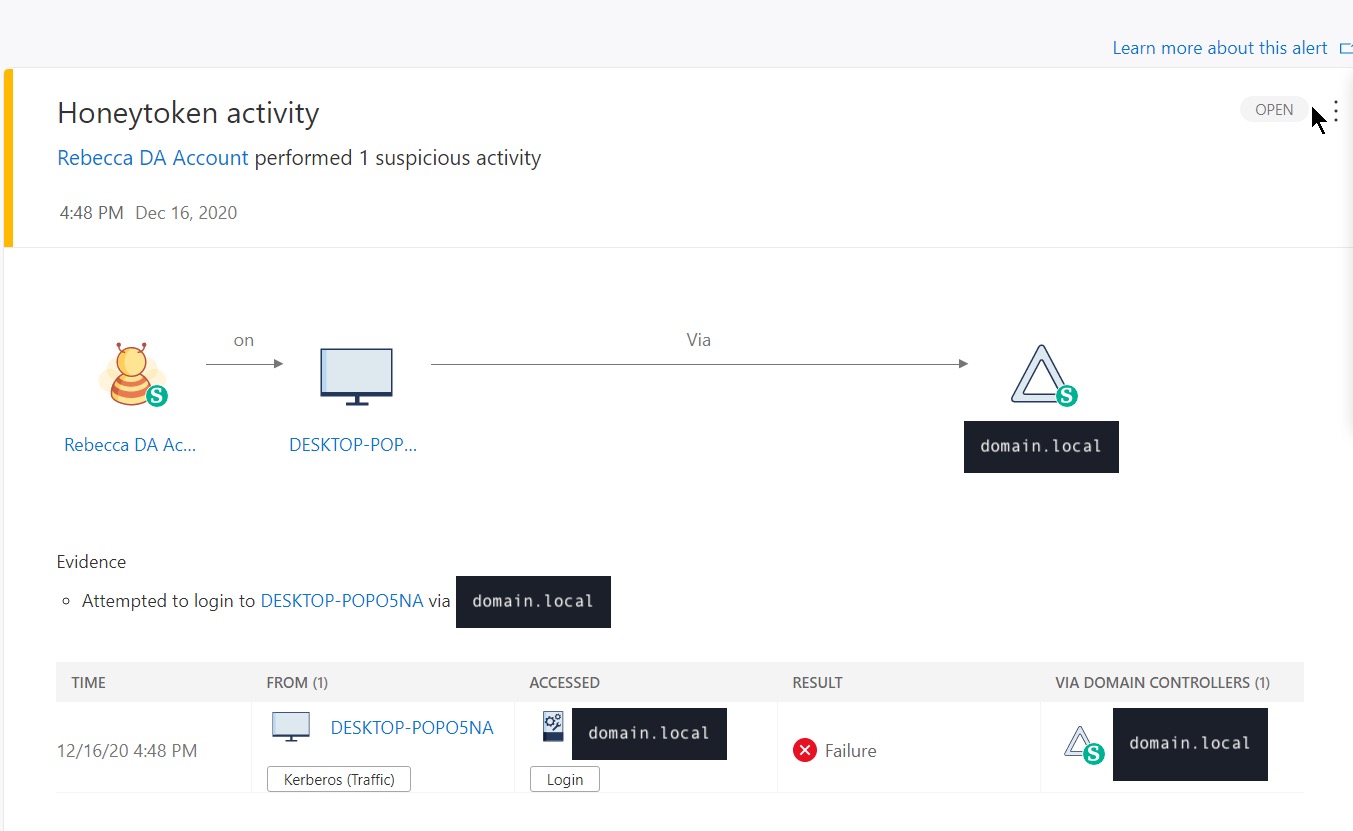
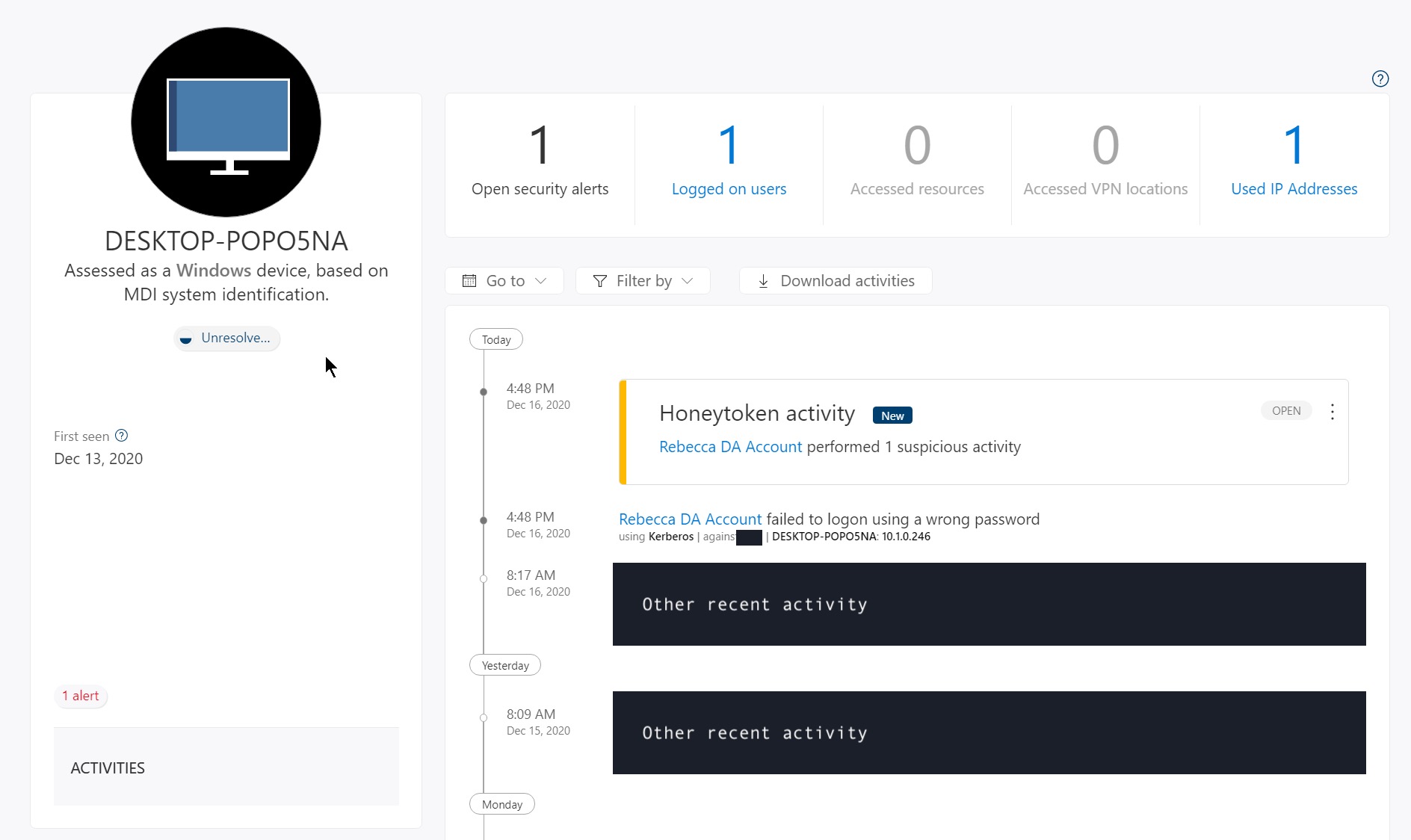
You can also interact with the user, “compromised” device and where the attacker was trying to get to, each of which gives you additional information about other failures that have happened - which could be helpful in an incident but doesn’t replace a SIEM or SOC because the information available in this view is veryyyy limited:
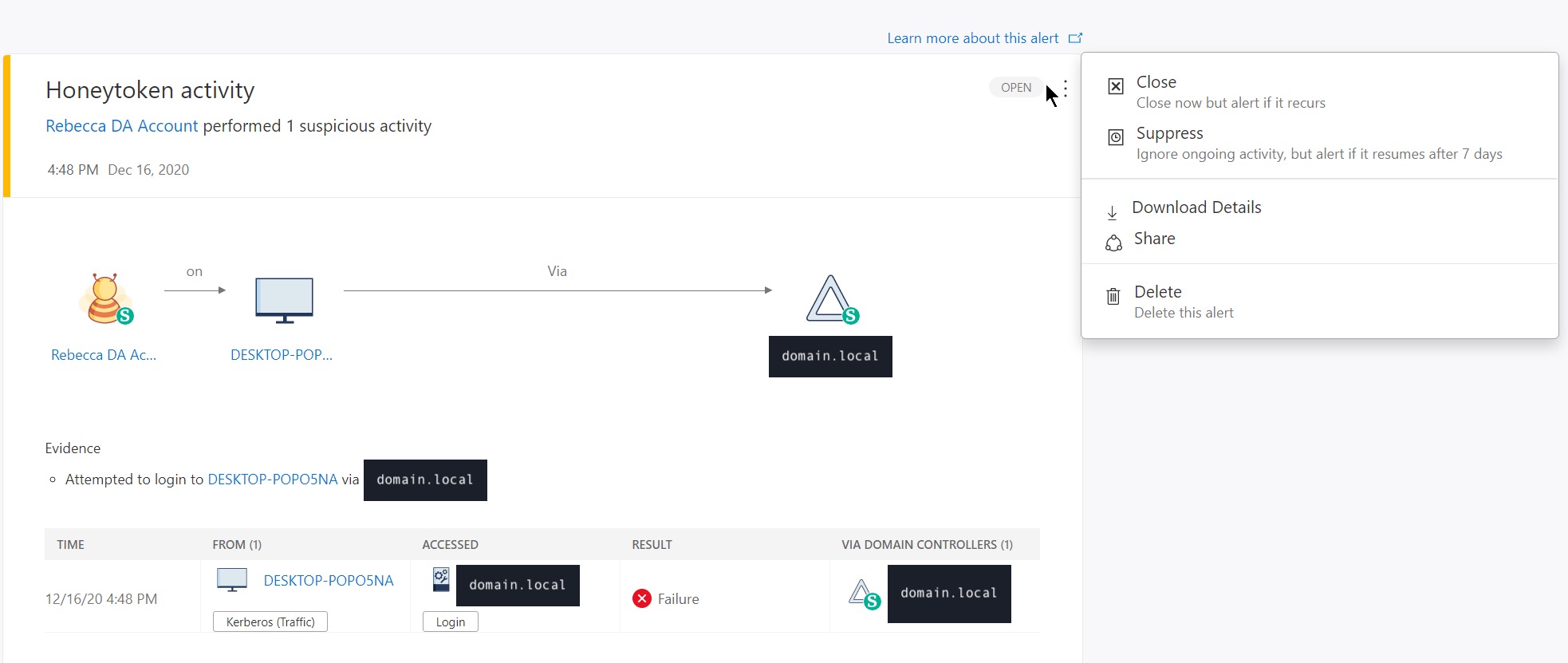
You can also close or suppress the issue from here by clicking the little arancinis:
Now if you have a Cloud App Security license, you can also investigate and resolve this issue from there!
🔎 Cloud App Security¶
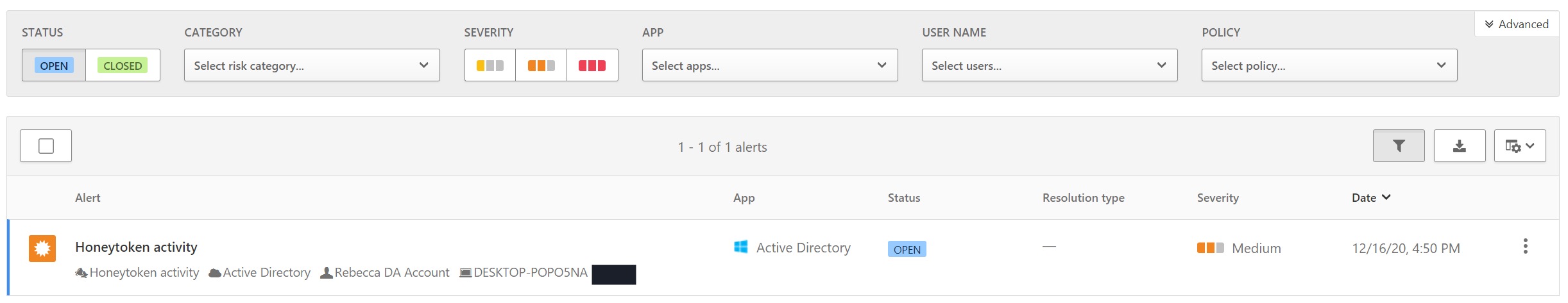
In a similar way to Defender, when you login to the Cloud App Security Portal you will be greeted with a little red one on the alerts tab and depending on your dashboard may see an open alert. But in a similar way to Defender, when you click through to view the active alert you will be given a summary of the issue:
Which when you click through gives you more detail about the event:
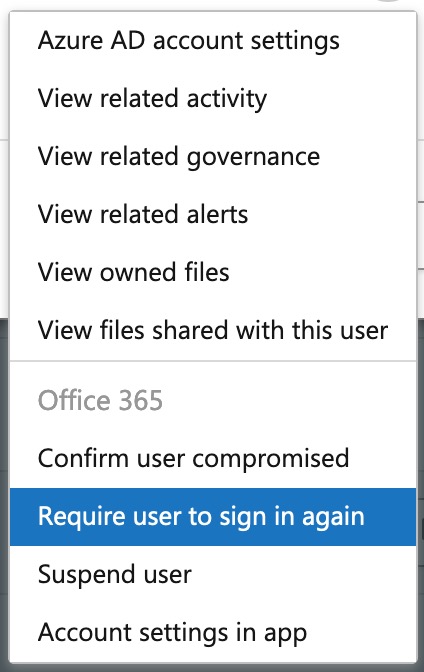
The thing that I like more about this portal though, is over on the right, if you click the arancinis associated with the user/account, you get a lot more actions that you can perform including suspending the user and marking them as compromised which depending on how your incident response processes are structured can be very helpful.
👋🏼 Conclusion¶
In conclusion, I hope you’ve enjoyed this little speed run through setting up canary tokens in Office 365 - I think they are a super powerful feature for organisations that have the budget to buy Microsoft Defender Licenses and the integration with Cloud App Security is also really nice.
This will be my last blog post of 2020, I hope you get through another day, week, month and year, even if it just means you exist.
♥️ errbufferoverfl